Endpoint Protection in Configuration Manager provides basic management of the Windows Defender Firewall on client computers. For each network profile, you can configure the following settings: Enable or disable the Windows Defender Firewall. Block incoming connections, including connections in the list of allowed programs.. Malwarebytes Endpoint Protection is an endpoint security solution built to protect against advanced threats. Endpoints are one of the most common means of access for malicious attackers. Each one.
ENDPOINT (DESKTOP & SERVER) SECURITY Got Your Six Cybersecurity

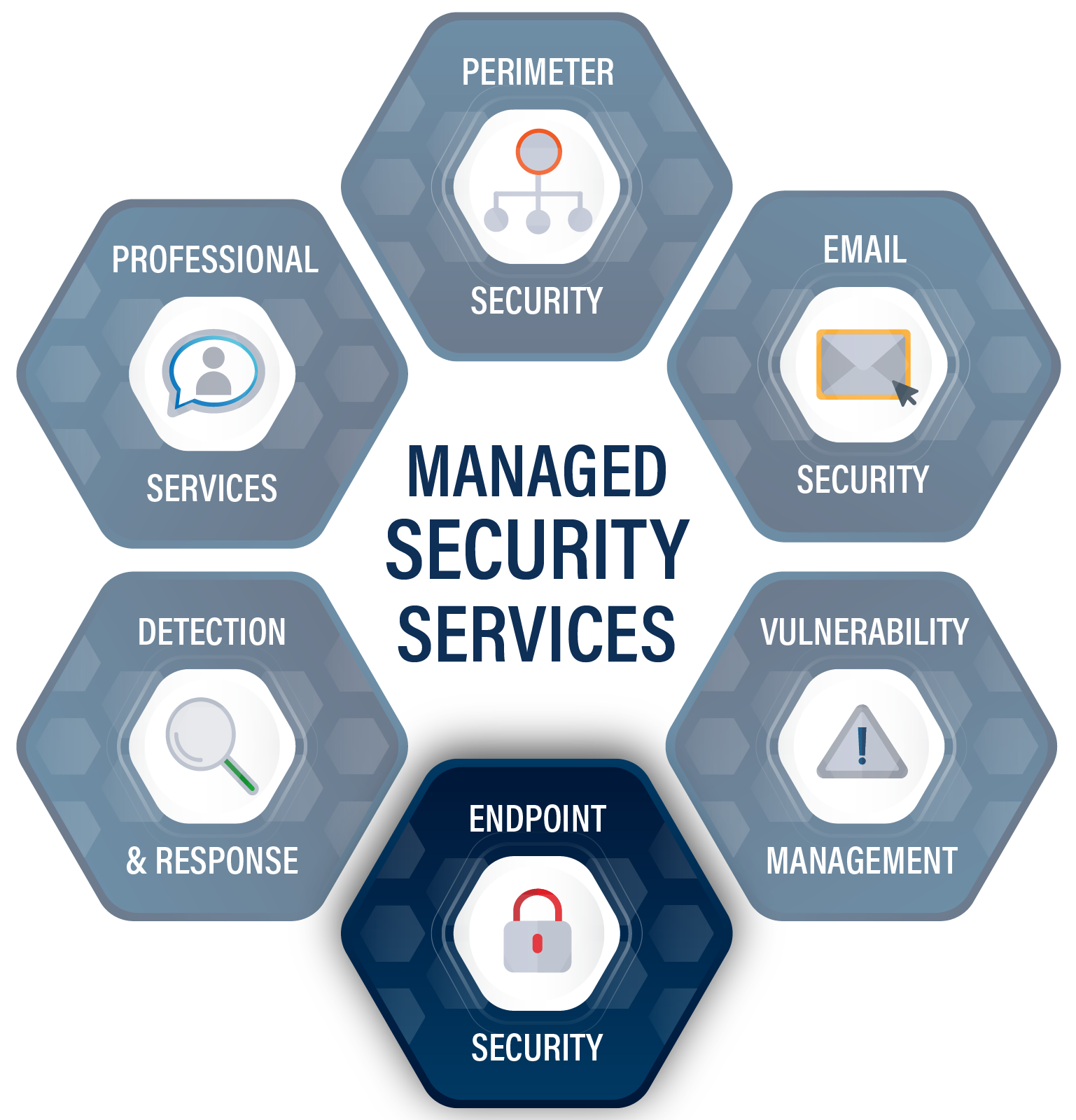
Endpoint Security and Protection

Microsoft Endpoint Manager Enable Endpoint Protection Microsoft Tech Community

Managed Endpoint Protection Service SBC Solutions

Best Endpoint Protection SearchInform

10 Best Endpoint Protection Solutions Comparitech

SYMANTEC ENDPOINT PROTECTION Interfacing the SEPM with Protection Cen…

Toshiba Tec Endpoint Protection

Getting started with Sophos Endpoint Protection YouTube
Managed Endpoint Protection Digitalera group

Der Endpoint Protection Service für Unternehmen

Endpoint Security Today’s Cybersecurity Is Endpoint Protection New

Toshiba Tec Endpoint Protection

The Goal Of Endpoint Security Uniserve IT Solutions
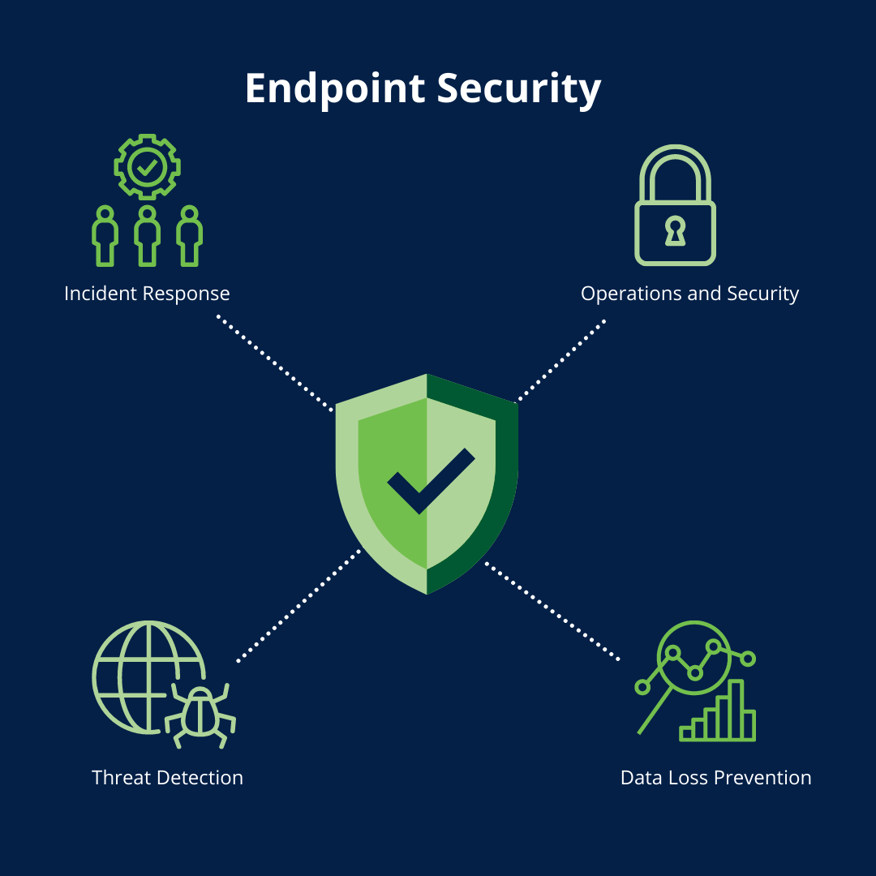
The Ultimate Guide to Endpoint Security Top Endpoint Security Solutions (2021)

SNC Endpoint Protection Service SIEVERSGROUP

What's the Best Microsoft Endpoint Protection Service?

Endpoint Protection Antivirus ASC Services Botswana
ENDPOINT PROTECTION SERVICES (EPS) METCLOUD

SentinelOne's new Deep Visibility capability enhances endpoint protection
Endpoint protection involves monitoring and protecting endpoints against cyber threats. Protected endpoints include desktops, laptops, smartphones, tablet computers, and other devices. Various cybersecurity solutions can be installed on and monitor these devices to protect them against cyber threats regardless of where they are located on or.. Endpoint security, or endpoint protection, refers to securing endpoints — such as desktops, laptops, and mobile devices — from cybersecurity threats. Endpoints can create entry points to organizational networks which cybercriminals can exploit. Endpoint security protects these entry points from malicious attacks.